
Be a Step Ahead of the Hackers
In accordance with OWASP's top API security risks, we build our security solutions to protect your API endpoints from the prying eyes of hackers.
With XecureAPI Gateway, streamline your operations and protect your API services by elevating the overall API ecosystem. Our cutting-edge API Gateway Security solutions fortify the digital landscape and empower businesses with robust security measures through advanced API features.
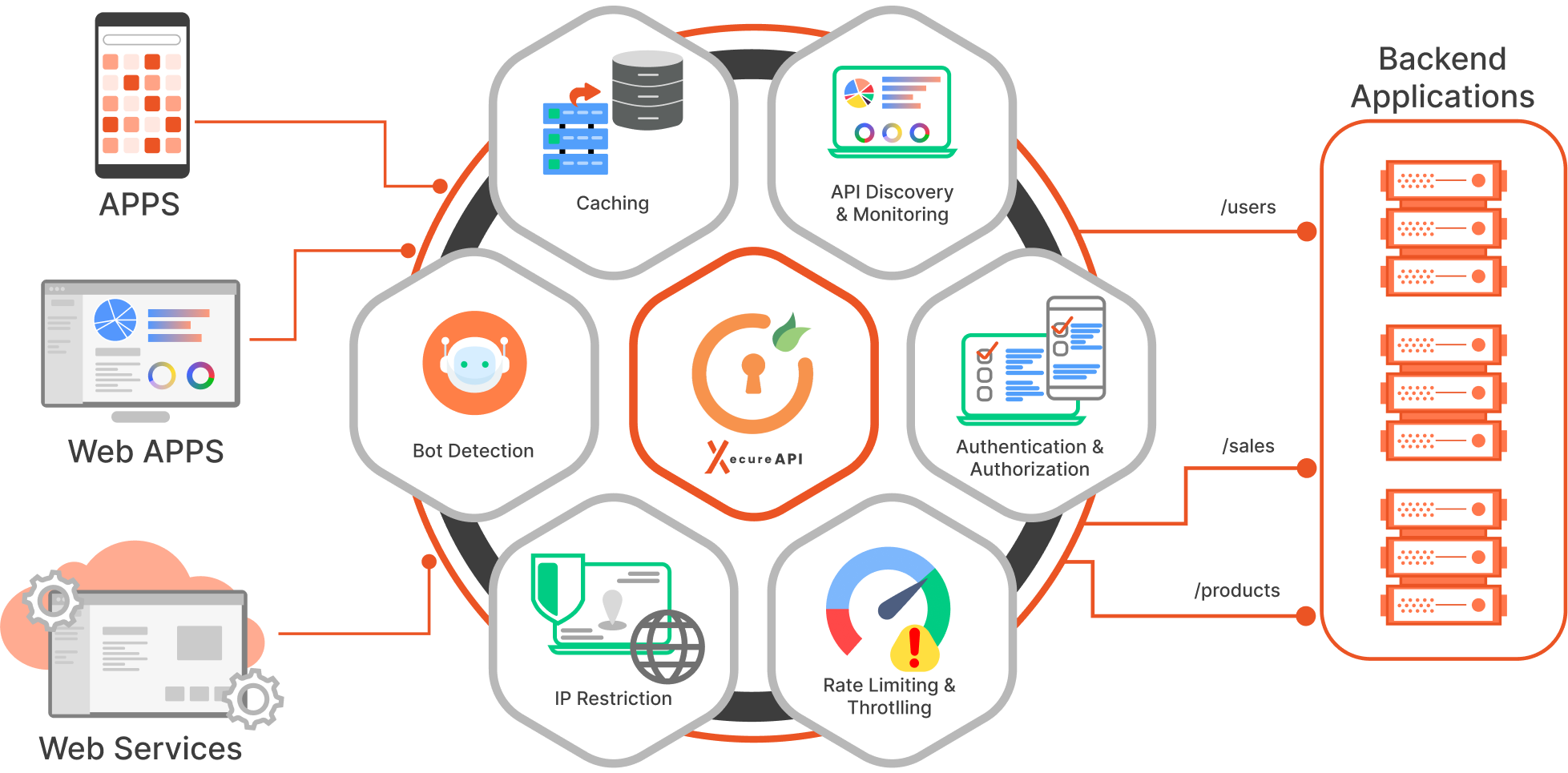

Our Security Features to Protect Your APIs
Safeguard your sensitive data and maintain the trust of your customers with XecureAPI Security features:
- API Authentication
- API Authorization
- Monitoring and Analytics
- Rate Limiting & Throttling
- Load Balancing
- Caching
- Protocol Translation
- API Aggregation
- IP Restriction
- CORS
What is API Authentication?
API Authentication helps verify the identity of every user trying to access the API. We implement various API Authentication methods to confirm the user's identity. These include:
How is API security ensured using API Authentication?
API security is ensured through the robust API authentication methods mentioned above. These methods secure communication channels by validating user credentials. Additionally, API tokens, associated with user accounts, manage access scopes. Regular security audits, rate limiting, and secure token storage contribute to a comprehensive API gateway security strategy, safeguarding against unauthorized access, data breaches, and potential vulnerabilities.
Protect Your Application/Services With XecureAPI Gateway in Just 3 Steps
1
Log In
1
Log in to the XecureAPI Dashboard.
2
Configure
2
Configure Services and Map Route.
3
Apply Policies
3
Apply policies as per your requirement and go live.
API Security is Not a One-Time Effort But an Ongoing Commitment!
Take your business to the next level with our robust API Gateway Solutions and API Security Solutions. Together, we can ensure that your APIs remain a secure and reliable gateway for your digital operations, fostering trust, compliance, and growth in an ever-evolving digital landscape. We look forward to assisting you on your journey to a more secure future!
What Sets XecureAPI Gateway Apart When it Comes to API Security?
Safeguard your sensitive data and maintain the trust of your customers with XecureAPI Security features:
Less Downtime
Say goodbye to downtime frustrations! We ensure easy configuration and provide rapid server adaptation to the new configuration providing minimal downtime and an impeccable transition to the updated environment.
Intuitive Dashboard
Be a technical or a non-technical user, our API dashboard is easy to use with every functionality defined clearly.
Free Trial
It's important to know the product before buying it. Thus, we offer a trial of the complete solution so that you can use it exactly how you would after purchasing it.
Extensive Setup Guides
We value your time and efforts. Hence, we provide easy and precise step-by-step instructional videos and setup guides to help you configure the API Gateway within minutes.
Customizable Solutions
We do not follow the one size fits all approach. Every business is different and hence their needs. If you require any customizations in the API Gateway, we offer custom-built solutions to meet the specific needs of our clients and organizations.
24*7 Active Support
Issues don't follow a clock to arise and we understand that. We have a dedicated support team at your disposal, 24*7. Get instant help or have debugging sessions with our engineers to take a look at any issues you may face.
Request a Live Demo
Fill the form and get a free demo from XecureAPI

Learn More About Our API Gateway and Security Solutions
Frequently Asked Questions
What is API Security?
What is the importance of API Security?
What are the different security risks and attacks associated with APIs?
What are the different approaches and solutions for improving API security?
What is the XecureAPI gateway?
What are the key measures to protect my APIs?
Resources
Blogs
Get the latest news, insights, and information about XecureAPI API Gateway.
Features
API security can be made easier with unified API gateway and security features.
Use Cases
XecureAPI ensures security and best performance in various use cases, such as load balancing, API management, and authentication.
See more

