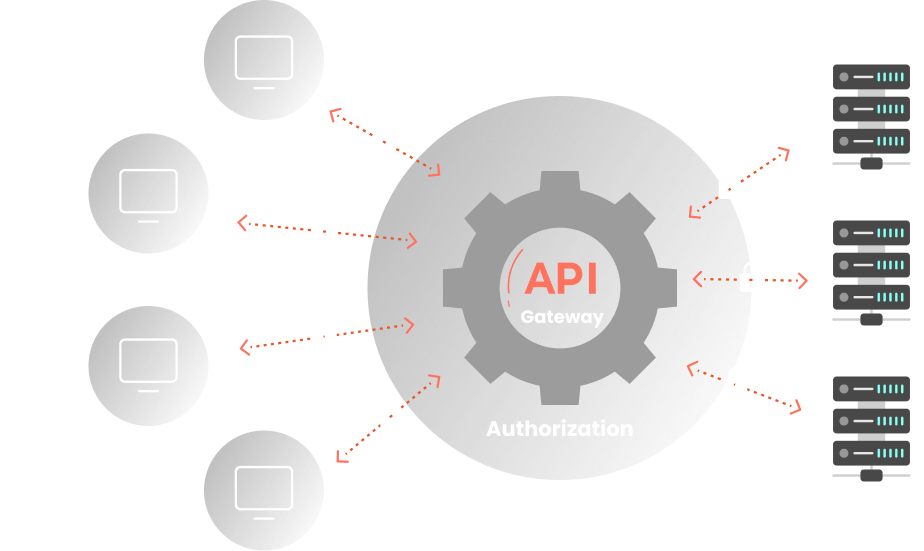
XecureAPI Gateway Authorization Process
Allow access to only authorized users to secure your application and resources with our robust API authorization process.
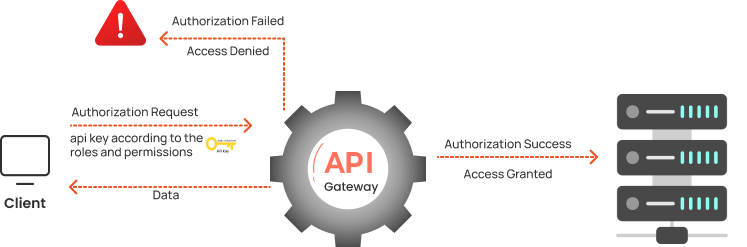
- Once the user is authenticated, the server checks the parameters to verify and validate the request against the authorization rules.
- Our authorization rules and policies will determine whether the user has access to the specified resource or not.
- These rules can be role-based, attribute-based, or a combination of both.
- If the user complies with the authorization rules, access is granted to the requested resources, otherwise, it is denied.
Our API Authorization Methods
Role-based API keys
Manage and control the access to APIs based on roles or permissions using our role-based API keys for API authorization.
- You can define which roles and permissions are required to access your APIs in the API gateway.
- Based on that we determine which roles are allowed to access which part of APIs.
- Using API gateway we provide API keys based on roles and permissions, which can be further used for user verification.
- When a user creates an API request with the API key, our gateway receives the request and verifies the roles or permissions associated with the API keys.
- If all the roles or permissions are valid then access to the given resource, otherwise it is denied.

OAuth:
Implement our three-legged OAuth flow to manage and control different access levels and permissions.
- A user initiates the process by creating an application in the API gateway, and our gateway will issue a client ID and client secret for further processing.
- The client application initiates the flow by sending the client ID and client secret for verification to the gateway. It is subsequently redirected to the login page.
- The user authenticates themselves and grants the consent screen. As a result, the gateway sends back the authorization code to the redirected URL.
- The obtained code is then exchanged for an access token.
- Next, when accessing the resources this user access token is sent along with the API request. API gateway verifies the access token validity and associated permissions.
- If all checks out, the API gateway shares the requested resource data based on the granted permissions.
LDAP
Use your LDAP server to manage and control access to your APIs based on the LDAP security groups with our LDAP Authorization.
- You can define which LDAP security group a user should be a part of to access your APIs in our API gateway. Multiple security groups can also be configured, allowing fine-grained access control.
- When a user initiates an API request, they authenticate themselves by sending their LDAP credentials.
- The API gateway then performs user authentication and verifies whether the user is a member of the LDAP security group that has been configured for the requested API.
- If all the conditions are satisfied, the user is given access to the requested resource data.

What Sets Us Apart?
- We keep the API authorization policies and documents up-to-date
- We log all API authorization requests and decisions
- We use secure communication to transmit data
- We ensure secure storage for keys and tokens
- We offer developer-friendly integration for API authorization
- We set a reasonable expiration time for access tokens
- We provide support for LDAP as well as LDAPS protocols to communicate with your LDAP server.
- Along with anonymous bind, we provide an option for regular bind operation, enhancing overall security for your LDAP server.
API Security is Not a One-Time Effort But an Ongoing Commitment!
Robust Security
With our cutting-edge authentication and authorization methods, we ensure that your APIs are protected against unauthorized access and data breaches.
User-Friendly Integration
With the help of our easy-to-follow documentation and the support of our developers, we make the integration process seamless for your existing systems and applications.
Scalability
Our solution scales with your needs. So, don't worry about security vulnerabilities when you grow your applications and user base.
Real-time Monitoring
Gain insights into API usage with comprehensive monitoring and reporting to instantly identify and respond to suspicious activities.
Customizable
We can tailor our methods and policies to meet your specific requirements to help you adapt to evolving security standards and compliance regulations.
24 X 7 Support
We ensure that help is always available when you need it by offering timely solutions around the clock, giving you complete peace of mind.
Frequently Asked Questions
What is API Authorization?
Should API gateway handle API authorization?
How to apply authorization to the API endpoint?
Request a Live Demo
Fill the form and get a free demo from XecureAPI