Knowing the critical role of APIs in running any web application smoothly, their security cannot be ignored. Among various authentication methods, API key authentication is one of the crucial API security solutions.
API (Application Programming Interface) providers use API keys to monitor and manage their services. They play the role of a security mechanism. It's a code provided by an API provider to an application to authenticate the user and control access to their APIs. These codes are sent in alphanumeric format and can be used to prevent unauthorized access and manage interactions with their API.
Importance of API Key for Authentication
By now, we know the role of API keys; but, why is authentication with API keys necessary?
- API key authentication helps ensure that only authorized users can access an API. Without proper authentication, an attacker can easily access sensitive data.
- Managing and controlling access to the services is crucial as the API provider can issue permissions at various levels. This can allow detailed control over who can access the specified endpoints. If no proper authentication mechanism is in place, anyone can access any API end-point, making them vulnerable to attacks.
- API keys allow you to track and monitor API usage. We can detect any suspicious activity by observing patterns related to API calls associated with each API key. As a result, these patterns enable us to detect and stop attackers in a timely manner.
- API keys enable rate limiting, which limits the number of times an API can be called. If an attacker is planning to overwhelm the system using a DDoS attack, rate limiting can prevent it.
These are a few benefits of API key authentication among many others. To summarize the benefits of an API key, it can be called a fundamental aspect of managing and securing APIs which facilitates efficient and secure interactions between applications or servers.
Best Practices for API Key Authentication
Just the implementation of API keys for authentication doesn’t cover it all. Deploying proper API security solutions is equally important. Listed below are a few best practices that every API provider must follow to secure API endpoints and run a system smoothly and securely.
Keeping the API key as a secret: API keys must be treated as passwords and thus need to be stored securely. So, it would be a bad idea to store the keys in plain text or encrypted format. The ideal way to store it as a hashed value.
Using HTTPS for API requests: Using HTTPS to encrypt data exchanged between clients and API servers is one of the ways to establish secure communication. This way, unauthorized users cannot intercept sensitive data during transit.
Using the same keys for a prolonged period: Using the same keys for a long period makes them vulnerable. New keys must be generated to mitigate the risks of unauthorized access.
Implementation of Rate Limiting: As mentioned above, limiting the number of requests is crucial so that no bad user spams your server with an overwhelming number of requests. Hence, to keep your application healthy, restrict the number of requests an application can make within a set timeframe.
Monitoring and Logging: It's necessary to keep a log of the API requests and it's equally important to monitor the usage. Keeping track of API requests can provide valuable insights into the performance, security, and usage of the API and the underlying system.
All in all, adhering to these API authentication best practices can enhance your API security and protect it from the prying eyes of attackers.
Benefits of Using API Keys for Authentication
Using API keys as an authentication and authorization mechanism offers several benefits for both API providers and consumers. Listed below are a few advantages of using API Keys:
Improved Security: By now we’ve established that API keys add a layer of security to the APIs. The keys can be used to authenticate access to an API and can authorize access to sensitive data. Further, with API keys and monitoring features, malicious activities can also be detected and prevented in advance.
Improved Performance: With API keys for authentication, data from the APIs can be cached which can help minimize the number of requests and improve the performance. Authentication with API keys also helps in load balancing which helps distribute the requests across multiple servers, without overloading just one. Developers can also monitor the performance of the API and optimize it accordingly.
Increased Flexibility: Developers can customize the API keys that can offer unique access per key. Also, using API keys, other APIs can be connected which can allow exchanging data across various applications. Testing and versioning can help check the functionality and performance of APIs before deployment and create different keys for different versions respectively.
What are the Different Types of API Keys
-
Public API Keys: Public API keys are authentication credentials that are intended to be openly shared and used by external clients to access specific resources or services. These keys are typically used when the API provider wants to grant access to certain functionalities or data to a wide range of developers, applications, or users without requiring individual authentication for each user.
-
Private API Keys: Private API keys for authentication play a crucial role in securing APIs and preventing unauthorized access. They are typically used in conjunction with other authentication mechanisms, such as OAuth, JWT, or HMAC, to validate the identity of the application or service accessing the API.
-
Scoped API Keys: Scoped API keys are a type of API key that comes with specific access permissions limited to a defined scope or set of resources within an API. Unlike a generic API key, which might grant access to all endpoints and functionalities, scoped API keys are tailored to allow access only to certain parts of the API.
API Key Authentication Methods Can Protect REST APIs from Which Risks?
Two of the major vulnerabilities from which API Keys can protect API Gateways include:
- Broken Function Level Authorization.
- Broken Authentication.

Let’s get an insight into how API Key Authentication can prevent these attacks.
Broken Function Level Authorization:
Broken function level authorization is a security vulnerability that occurs when an application does not properly enforce access controls on specific functions. It stands at the 5th position in OWASP's top 10 API Security Risks in the 2023 list. To prevent this, authentication with API keys can be used to validate user permissions at every relevant function or resource access point. Proper authentication, authorization checks, and careful validation of user input to ensure that only authorized users can perform specific actions can prevent the API from this attack. It is important to note that in the mitigation of both risks, API key authentication plays a significant role. But to improve API security, it is imperative to implement other security methods.
Broken Authentication:
An account-specific session ID is created when a user logs into an account. If an application is not created securely in terms of authentication, then the attacker can use several ways to misuse the application. When authentication is broken, attackers can exploit weaknesses in the process to gain unauthorized access to the application This is the second riskiest attack as per OWASP's top 10 API Security Risks. API keys separate user credentials from access control, enhancing security by offering a distinct authentication method. API keys can be confined to specific actions and revoked without affecting other parts of the system which can limit the potential damage that can happen if the key is compromised.
Implementation of API Key Authentication
How are API Keys Generated?
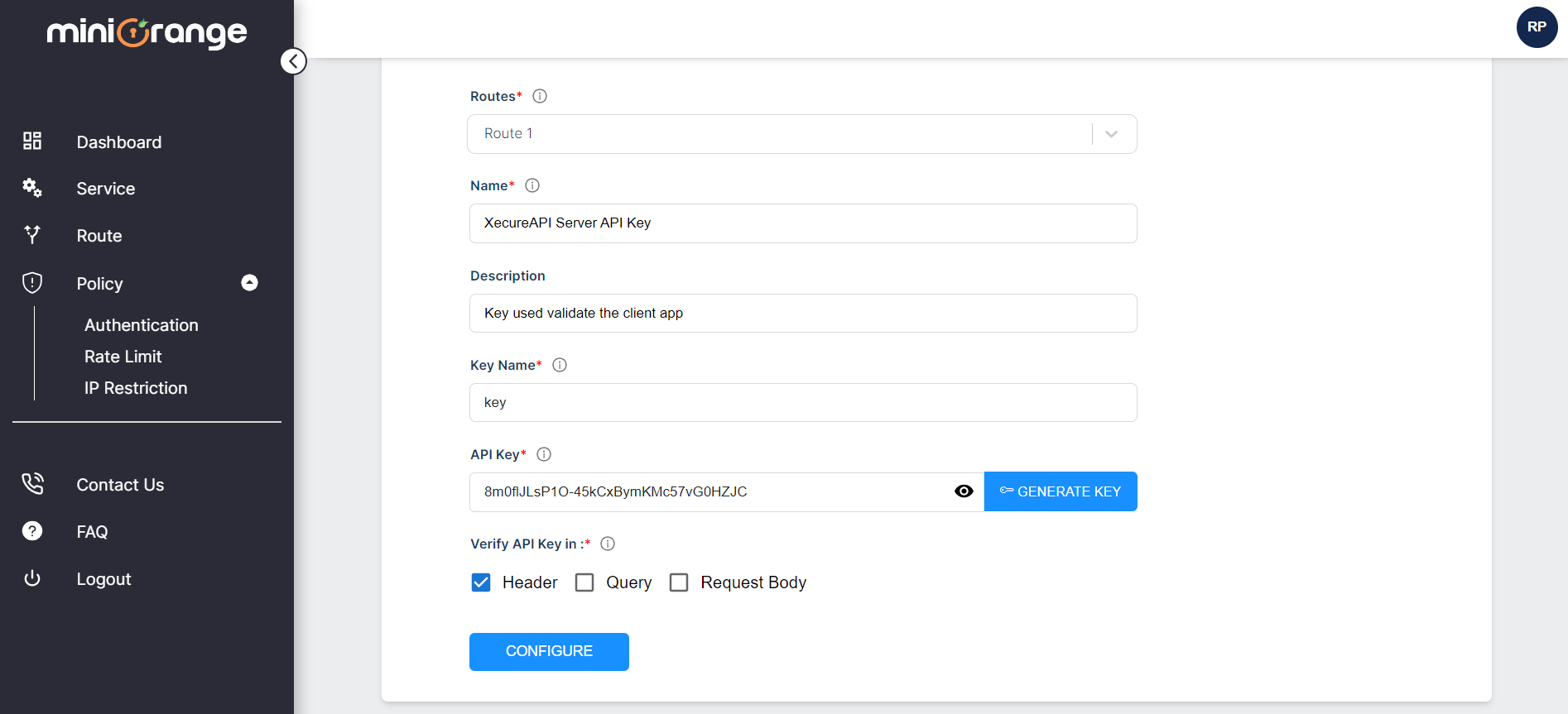
API keys for authentication can be generated using our Xecure API Dashboard. Within the dashboard, you will find the option to generate API keys in the policy section. We provide the capability to generate unique API keys for each application.
How to include API Keys in Requests?
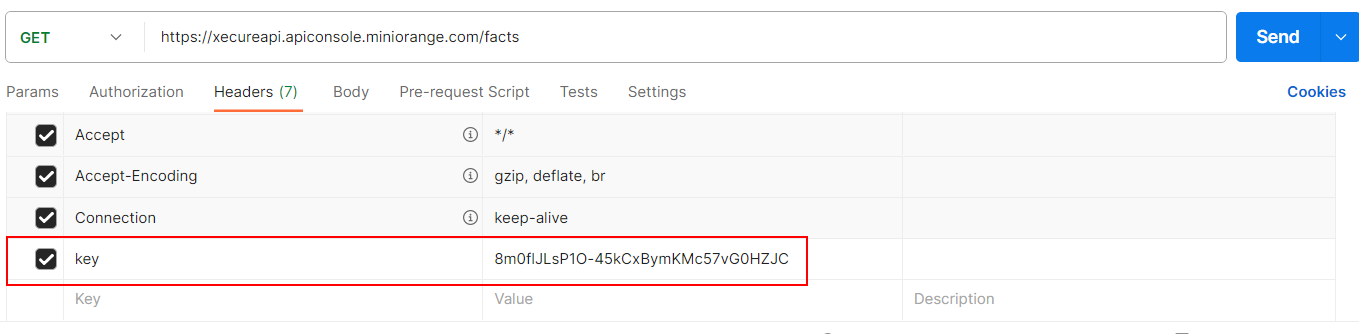
API key holders should include these generated API keys in their API requests. Key holders have the flexibility to send the API keys through headers, query parameters, or payloads.
How are API Keys Validated on the Server?
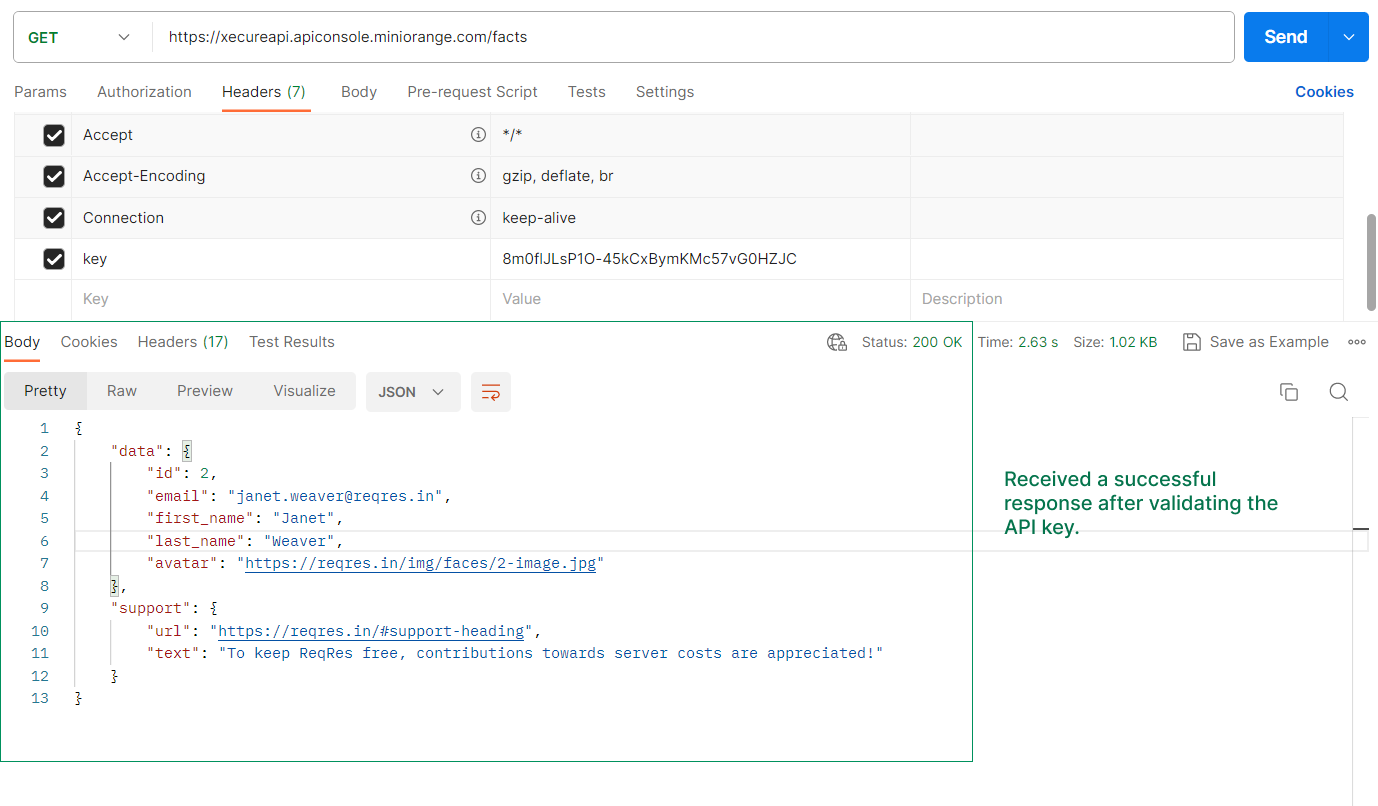
Upon receiving API requests, our gateway extracts the included API keys and performs validation to facilitate further processing.
To get a detailed understanding of how to implement API keys, go through XecureAPI’s API Key Authentication Set-up Guide.
Reach out to our experts to get detailed insights into XecureAPI’s API security solutions.


