Concerns regarding data breaches and cyber threats are increasing day by day as the digital landscape is expanding. In fact, as per an article by Forbes, there was a 286% increase in API exploits from the first to the second quarter of 2022. Looking at these numbers, it's clear that securing APIs has become imperative for businesses and developers.
This is where API authentication plays a pivotal role in safeguarding critical data and allowing only authorized users to access it. It can be called a foundation of a secure API ecosystem.
Fundamentals of API Authentication
The primary purpose of API authentication is to verify the identity of the users or applications that are trying to access the APIs. The authentication process ensures that only authorized users can call and interact with the API to minimize the risk of data breaches and unauthorized access.
It is important to note that every application needs a different level of security. Owing to this, XecureAPI offers different API authentication methods to cater to the individual needs of the client.
Listed below are various API authentication methods that can protect your APIs from any kind of malicious activity.
API Key Authentication
API key authentication is one of the most widely used authentication methods for protecting APIs. The process requires clients to provide a unique key/token to access the API. The key is generated by the API provider in the form of a long alphanumeric string. The key acts as identification which allows the API server to verify the identity of the user and applications and further decide if the access should be granted or denied.
Pros of API Key Authentication Method:
- Simplicity and Speed: API authentication using API keys is easy to implement as developers can integrate this method into their applications without taking a lot of coding effort. Coming to the process, API keys are sent with each request which makes the process efficient as it saves multiple round trips to establish a session.
- Granular Access Control: Specific API keys can be assigned for specific access levels and permissions. This gives fine control over which data can be accessed by the user and which is restricted.
- Easy to Revoke and Regenerate: API keys can be easily revoked as well as regenerated. In cases of security breaches, API keys can be invalidated which can prevent unauthorized access in time. Further, new keys can be generated just as easily without disrupting the entire functionality of the application.
- Scalability: In cases where a large number of clients want to access an API, key authentication is considered a well-suited option. Since no session state is maintained on the server side, it's easier to scale the system as traffic grows.
Cons of API Key Authentication Method:
- Limited Security: Although API authentication using API keys provides a basic level of security, it's not as robust as other methods. If an attacker successfully cracks an API key, the security of the API stands at risk.
- Key Management Challenges: Managing API keys can become difficult as the number of keys increases with the number of users. Expiration and rotation policies must be kept in check but that adds another layer of complexity.
- Difficult User Identification: It becomes challenging to identify a specific user when multiple users access the API through a single client. This can hinder user-specific analytics and logging.
Basic Authentication
Basic API Authentication, also known as basic auth, is one of the simplest methods to secure API endpoints. The process involves sending a username and password with every API request. The username and password are combined by a colon and then converted to base64 format. It is usually sent as a part of the HTTP header. After that, the server verifies the credentials against the database and grants access if they are valid.
Pros of Basic API Authentication Method:
- Ease of Implementation: API authentication with basic auth is one of the easiest authentication methods to implement. It can be integrated with minimal coding and set up the authentication process without extensive configuration.
- Compatibility: Basic auth is supported by various frameworks and HTTP clients. This makes it easily accessible to various development environments.
- Immediate Access Control: Basic auth provides an easy way to control access to specific API endpoints. The server can validate the username and password and accept and deny the request based on the role and authorization level of the user.
Cons of Basic API Authentication Method:
- Security Concerns: In the basic API authentication method, if the credentials are sent in plain text then it makes them susceptible to introspection. Further, if the connection is not encrypted, sensitive data can be exposed easily.
- Limited Protection: As it is a basic authentication method, it lacks advanced features. If the attackers succeed in cracking the usernames and passwords, they can easily access the API until the credentials are changed.
- User Experience: For every request, users are expected to provide the credentials. This can create a bad user experience which can further discourage them from using the application.
JSON Web Tokens
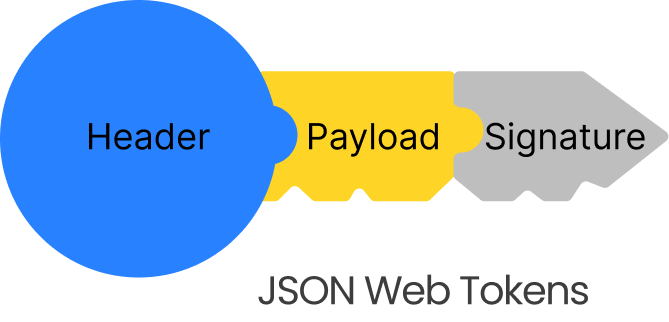
A JSON Web Token (JWT) is a method of securely transmitting data between servers as a JavaScript Object Notation (JSON) Object. API authentication with a token mostly consists of a header, payload, and signature. The header comprises the algorithm information that is used in generating the signature, while the payload carries the data and the signature ensures token integration.
Pros of JSON Web Tokens (JWT):
- Compact Format: JWT tokens can easily transmit data over headers, the body of the request as well as over the URLs as they are compact. Owing to their reduced size, they offer optimal performance and minimal overhead.
- Statelessness: While using JWT for API authentication, session data is not required to be stored which not only simplifies the server management process but also reduces the load.
- Versatile Usage: JSON web tokens are versatile as they can be used for authentication, authorization, and data exchange between applications.
- Secure Data Transmission: JWT offers integrity and authenticity of the data as they are digitally signed. This prevents the tokens from being tampered with by unauthorized users during transmission.
Cons of JSON Web Tokens (JWT):
- Limited Expiry Control: When the token is created, an expiration time is defined with it. The expiration time cannot be changed unless a new token is created which might cause access issues if it is not managed properly.
- Token Security: In API authentication using JWT, if the attackers succeed in cracking the private key, they can generate valid tokens and further misuse the data.
- Token Payload Exposure: The payload of JWT is not encrypted, hence, critical data should not be included in the payload. Although it is not readable, it is accessible to anyone who has a token.
- Revocation Challenge: The major challenge with JWTs is that they cannot be revoked once issued. They remain valid until the expiry. To revoke the access, additional mechanisms are required or the token lifetimes can be shortened.
OAuth 2.0
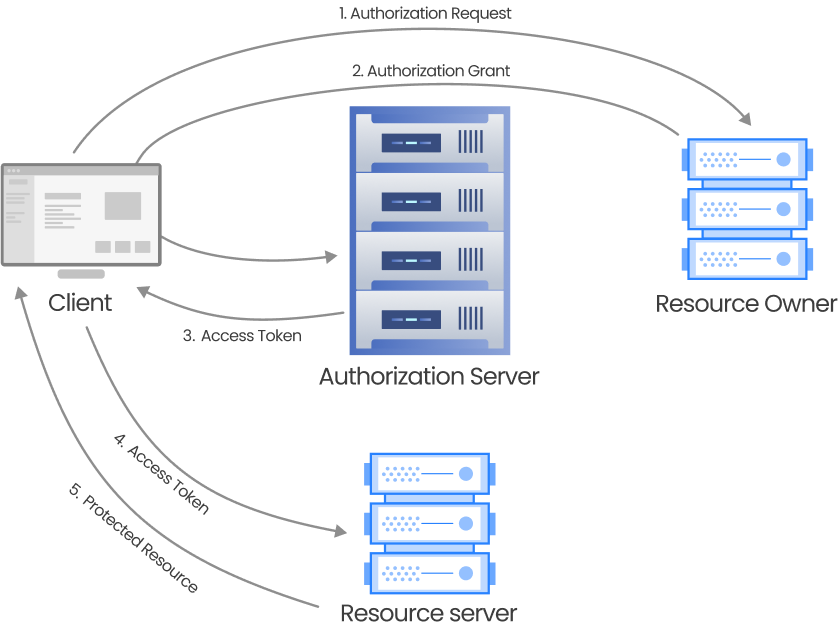
OAuth stands for "Open Authorization." This standard enables a client application to access information from third-party apps on behalf of a user. In this protocol, the user authenticates themselves through identity providers (IDPs) and grants access to specific scopes. Subsequently, the client application receives an access token, which facilitates the retrieval of particular information according to the specified scopes from the resources of other apps.
Pros of OAuth 2.0:
- Enhanced Security: Using OAuth 2.0 protocol for API authentication eliminates the need for sharing passwords with third-party applications as access is granted using tokens.
- Granular Access Control: Similar to API Key Authentication, OAuth 2.0 allows defining scopes and permissions which ensures that not only authorized users access the data but they can only access information that they are allowed to.
- User Consent: Before granting access, it is mandatory to get user consent. This ensures that the users have the authority to allow or deny access if they are aware of the data being accessed.
- Token Expiration: Just like in JWT, OAuth 2.0 tokens have limited lifetimes. This improves security as the chances of unauthorized access are reduced.
Cons of OAuth 2.0:
- Complexity and Security Configuration: OAuth 2.0 implementation is slightly more complex than other API authentication methods. Even the slightest misconfiguration can lead to vulnerability.
- Token Management: Token management in OAuth 2.0 must be done precisely as any inadequacies can cause security breaches or unauthorized access.
- User Experience: Although OAuth2.0 ensures a secure mechanism, the users are redirected to different applications through the authorization process. This can create a negative impetus for the user experience.
API authentication methods form the cornerstone of secure and seamless communication between applications in today's digital landscape. Each method, from the simplicity of Basic Authentication to the versatility of OAuth 2.0, the statelessness of JWT, and the efficiency of API keys, offers a unique approach to balancing security and usability.
Choosing the right authentication method depends on the application's requirements, sensitivity of data, and desired user experience. Reach out to the experts at XecureAPI to make an informed decision about which security method can protect your API efficiently.


