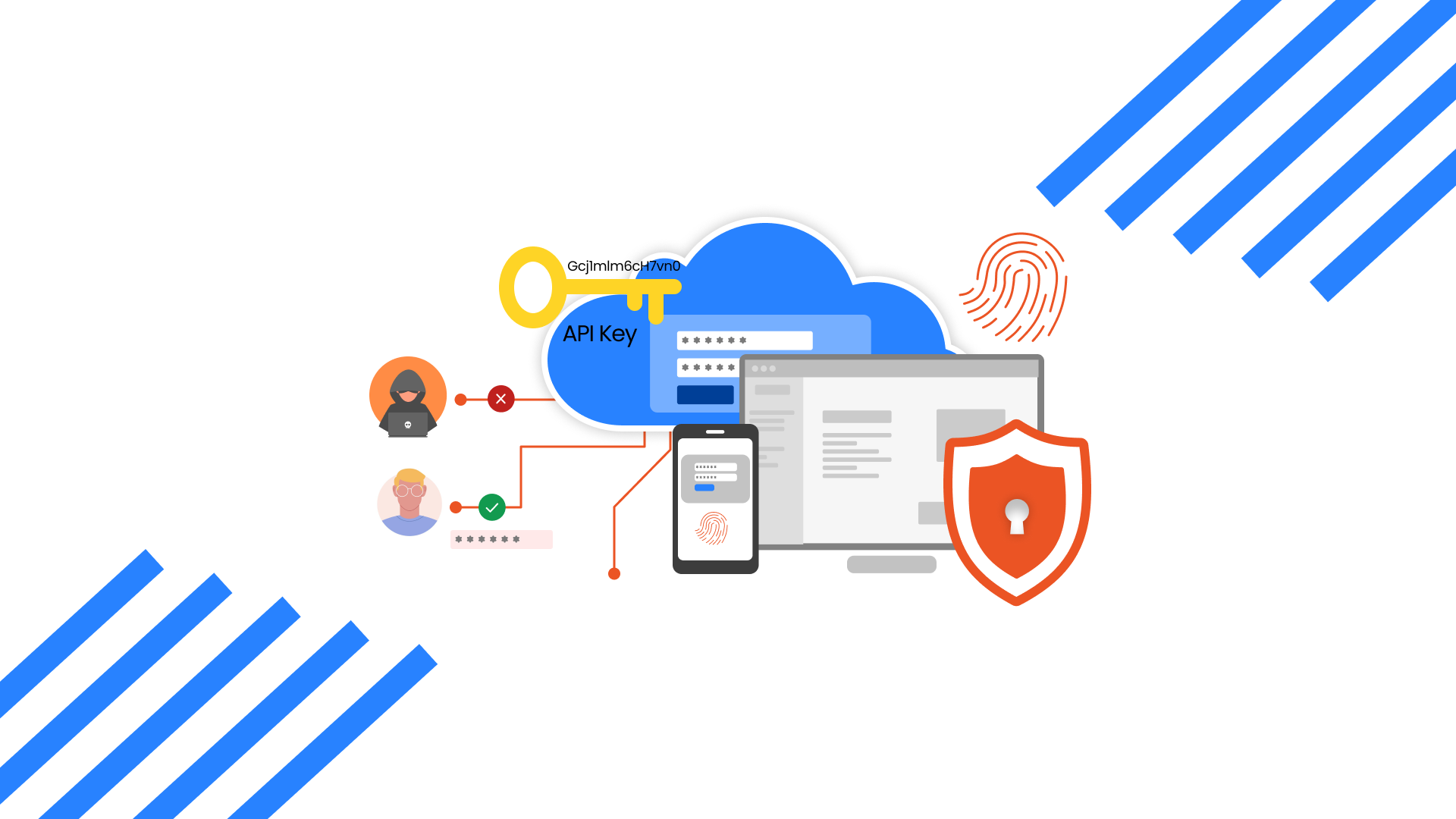
XecureAPI Gateway Authentication Process
Know the identity of the user or application trying to interact with your APIs with our robust authentication process.
- The communication is done with the APIs using identity credentials.
- The credentials are verified with identity information the server has on record.
- If the credentials are verified, access is granted to the user or application.
Our API Authentication Methods
We do not follow a one-size-fits-all approach! Our developers will help you select an authentication method that suits your business and application the best!
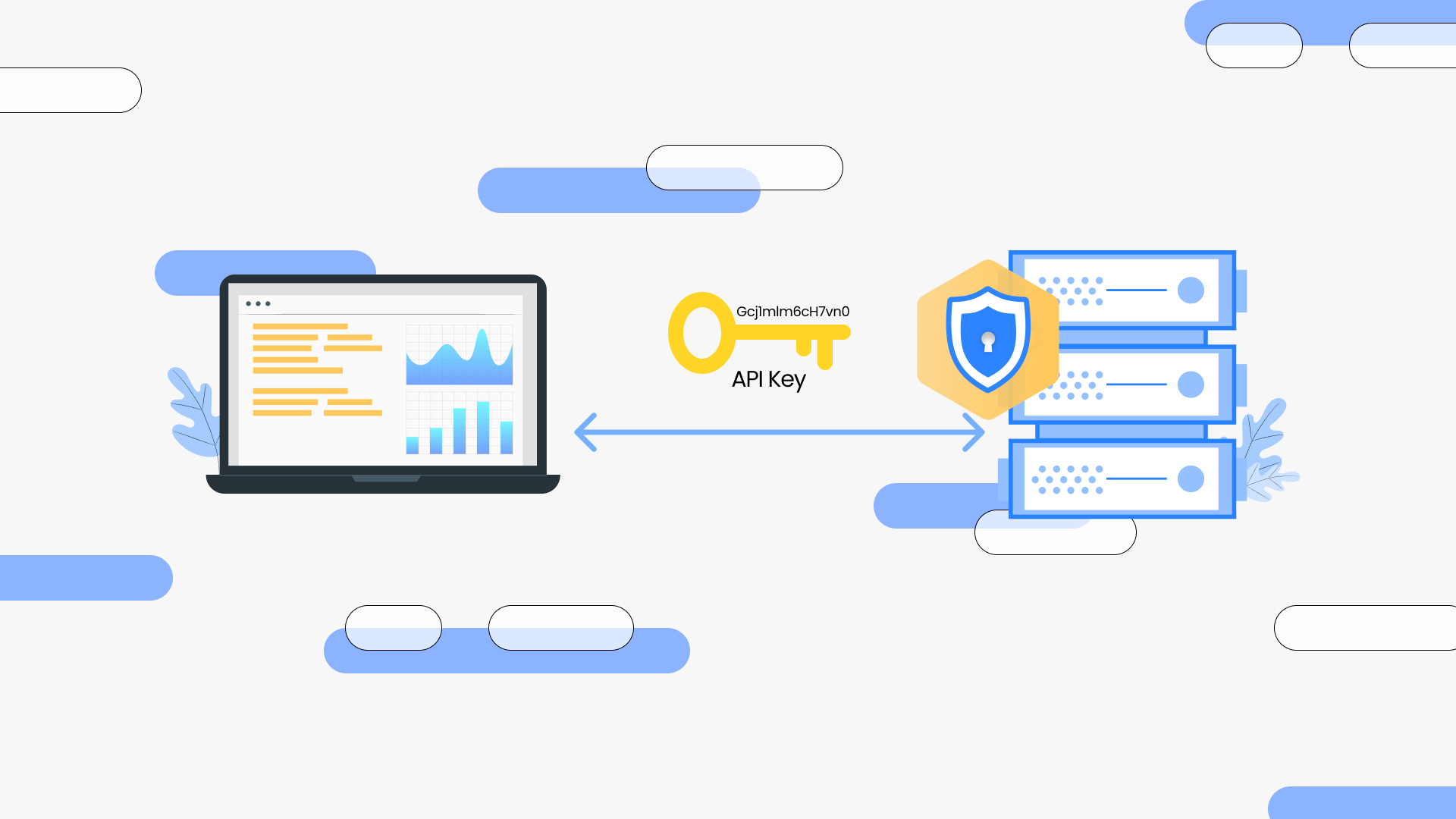
API Key Authentication:
Verify the identity of a user or application calling your APIs using our API keys
- The API keys are included in the request headers, body, or as a query parameter.
- Our API Gateway checks the received key against its database of authorized keys.
- If the API key is valid, the gateway processes the request; otherwise, it returns an error.


Basic Authentication:
Keep the API authentication process simple and sorted using our basic authentication process.
- The credentials (username and password) are typically included in the request headers in Base64-encoded.
- The API gateway validates the credentials against a user database.
- Access is granted if the credentials match, otherwise, it's denied.
OAuth (Open Authorization):
Utilize our OAuth protocol for a seamless and efficient API authentication and authorization process.
- It allows you to grant third-party applications limited access to your resources without sharing any credentials.
- Our API gateway will serve as a resource server and an authorization server. It can provide access tokens and validate them to access the resources.
- OAuth 2.0 is the most commonly used version and uses access tokens to grant access.


Token-Based Authentication:
Trust our token-based API authentication process to identify the user trying to access your data.
- A user or application can log in with their credentials, and our gateway will generate a unique JSON Web Token (JWT).
- The token generated by the API Gateway is returned to the user or application, which is then included in the headers of subsequent API requests.
- Our API gateway verifies the token's authenticity and expiration date.
- If the token is valid, the gateway processes the request further; otherwise, it returns an error message
LDAP Authentication
Our LDAP authentication for APIs process allows you to utilize your existing LDAP server credentials to authenticate.
- When a user or application calls an API, it includes authentication credentials in the request.
- API gateway acts as an LDAP client and initiates a bind operation to the LDAP server using the provided credentials.
- The LDAP server checks the provided credentials against its directory data.
- If the credentials are valid, the LDAP server responds with a successful bind operation.
- Based on the LDAP server's response, your API gateway determines whether the user is authenticated or not.

What Sets Us Apart?
- We use strong and unique keys and secure key storage
- We provide key versioning and emergency key revocation
- We use strong password policies and secure password storage
- We follow best practices for token storage
- We Offer Robust Token Issuing and Revocation Mechanism
- We Use Token Encryption and secure token storage
- We enforce strong password policies within your LDAP directory
- We use strong hashing algorithms to store user passwords securely
API Security is Not a One-Time Effort But an Ongoing Commitment!
Robust Security
With our cutting-edge authentication and authorization methods, we ensure that your APIs are protected against unauthorized access and data breaches.
User-Friendly Integration
With the help of our easy-to-follow documentation and the support of our developers, we make the integration process seamless for your existing systems and applications.
Scalability
Our solution scales with your needs. So, don't worry about security vulnerabilities when you grow your applications and user base.
Real-time Monitoring
Gain insights into API usage with comprehensive monitoring and reporting to instantly identify and respond to suspicious activities.
Customizable
We can tailor our methods and policies to meet your specific requirements to help you adapt to evolving security standards and compliance regulations.
24 X 7 Support
We ensure that help is always available when you need it by offering timely solutions around the clock, giving you complete peace of mind.
Frequently Asked Questions
Which API authentication methods does XecureAPI Gateway provides?
How does API authentication work?
What is API key authentication?
Request a Live Demo
Fill the form and get a free demo from XecureAPI