- In July 2022, Twitter, a famous social media platform reported a major API breach that exposed the data of 5.4 million users. - VentureBeat
- In December 2021, FlexBooker, a digital schedule platform reported a DDoS attack that caused widespread network outages and allowed the attackers to steal data of 3.7 million users. - ZD Net
Looking at these numbers of API attacks, developers should start securing their APIs immediately, if they have not. With a massive increase in API usage, the need to protect APIs from malicious activities is bound to increase. Among various ways of securing APIs, authentication is considered a crucial one. In this write-up, we will cover what we mean by API authentication, the benefits of API authentication, and various API authentication methods that will help in API security.
What is API Authentication?
The primary role of APIs is to help applications and servers communicate and share data. API authentication helps verify the identity of the system, application, or user that is trying to access the API. So, whenever a client application tries to call an API, the authentication process ensures that the user is actually who they claim to be. Now the question arises, why do you need an API security solution in the first place?
Benefits of API Authentication
The basic goal of API authentication is to safeguard a web application from attackers who are on the lookout for even the slightest vulnerability.
-
Data Security: The primary feature of API authentication is that it only allows verified users to access the data. This way, sensitive data is protected from unauthorized users or applications. By controlling access, verifying identities, and protecting credentials, API authentication prevents unauthorized access to sensitive data. This way the integrity and confidentiality of data are protected.
-
Data Privacy: Using API authentication, one can enforce access control. This will allow only specific users to access specific data by protecting sensitive data during transmission. Data privacy is enhanced by controlling access and taking user consent. This ensures that critical information of the user is protected from attackers.
-
Compliance and Regulatory Requirements: Organizations need to comply with various regulatory standards that are related to data privacy, access control, and security. Using API auth, organizations can meet these compliances and protect sensitive data. For instance, as per the General Data Protection Regulation (GDPR), an EU data protection law, organizations need consent for data processing activities. In such instances, API Authentication and authorization are paramount for the organizations to comply with.
-
Improved User Experience: As API authentication adds a layer of security, users rest assured that their information is handled safely. Organizations can also tailor the content and services based on the profile and historical data of the user, providing them with a personalized experience. Apart from the aforementioned, there are various other benefits of API authentication. But to summarize it in a statement, we can say that if one wants to safeguard their web applications from any kind of online fraud, protecting the APIs is a must. But how to secure an API? To get an answer to this question, we need to understand the different API authentication methods.
API Authentication Methods
XecureAPI offers various authentication methods to protect your API from any attack. Depending on the requirements and application, one can choose the suitable methods.
Basic Authentication:
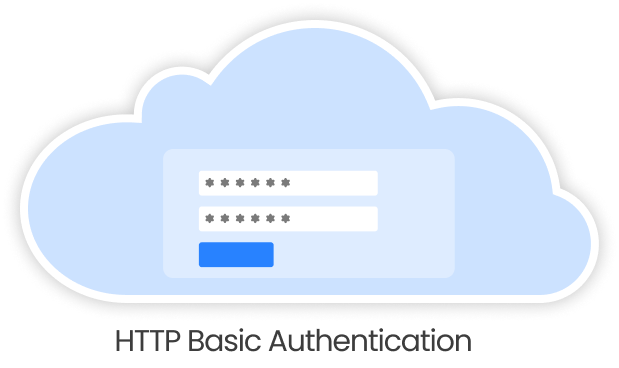
Basic API authentication, also known as Basic Auth is one of the simplest methods of verifying API requests. In this authentication method, a combination of username and password is sent in the HTTP headers of the request which are encoded in Base64 format. It is crucial to note that it is a basic authentication method and is more suitable in scenarios that do not require strong security. To protect your APIs from attackers, adding multiple security features is always advised.
API Key Authentication Method
API key authentication is a token-based authentication method that requires the user/client application to provide a unique key in their request. Every client is assigned a unique API key which is included in the request header. The server then uses these keys to authenticate the user and provide necessary API resources.
However, it is important to note that while managing a large number of clients, managing API keys can be challenging. Also, there is a chance of the key getting exposed to a bad user. It is always safer to implement this method with a combination of other methods for securing your API.
OAuth 2.0
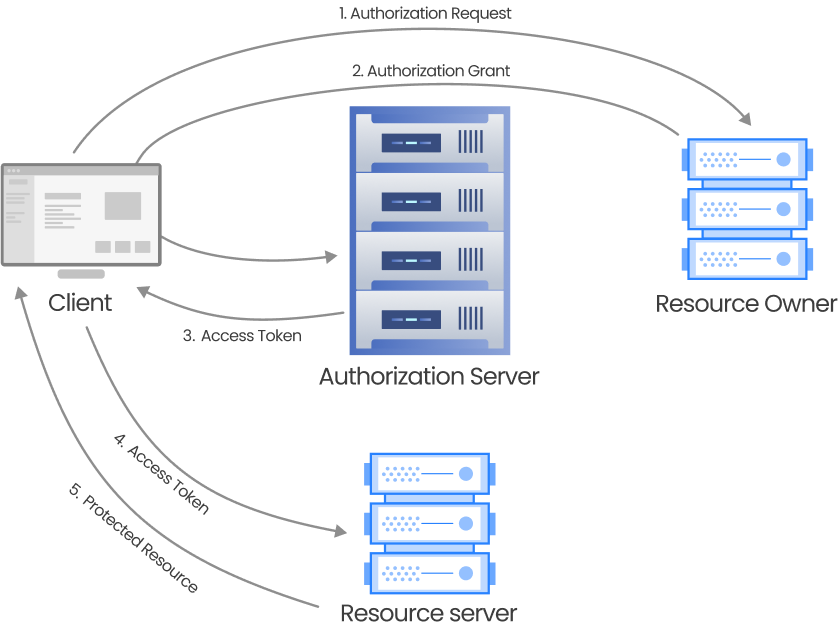
Open Authentication (OAuth) is used to authenticate third-party applications to access resources on behalf of a user. This API authentication method uses access tokens for verification. The process entails using various flows to generate access tokens which helps verify the user without sharing the actual credentials.
With OAuth 2.0, one can manage API authentication securely and flexibly, especially when third-party applications need controlled access to user resources. However, best practices and guidelines must be followed thoroughly during their implementation to secure your API completely.
JSON Web Tokens
JSON Web Tokens (JWT) is one of the popular API authentication methods that are often used with OAuth 2.0 flows. In this method, information is transmitted between two servers using JavaScript Object Notation (JSON) Object. As the name suggests, this is also a token-based authentication method.
Similar to OAuth, it is important to follow the best practices for JWT implementation including proper token validation, secure secret key storage, and other guideline, to protect API and user data.
LDAP Authentication
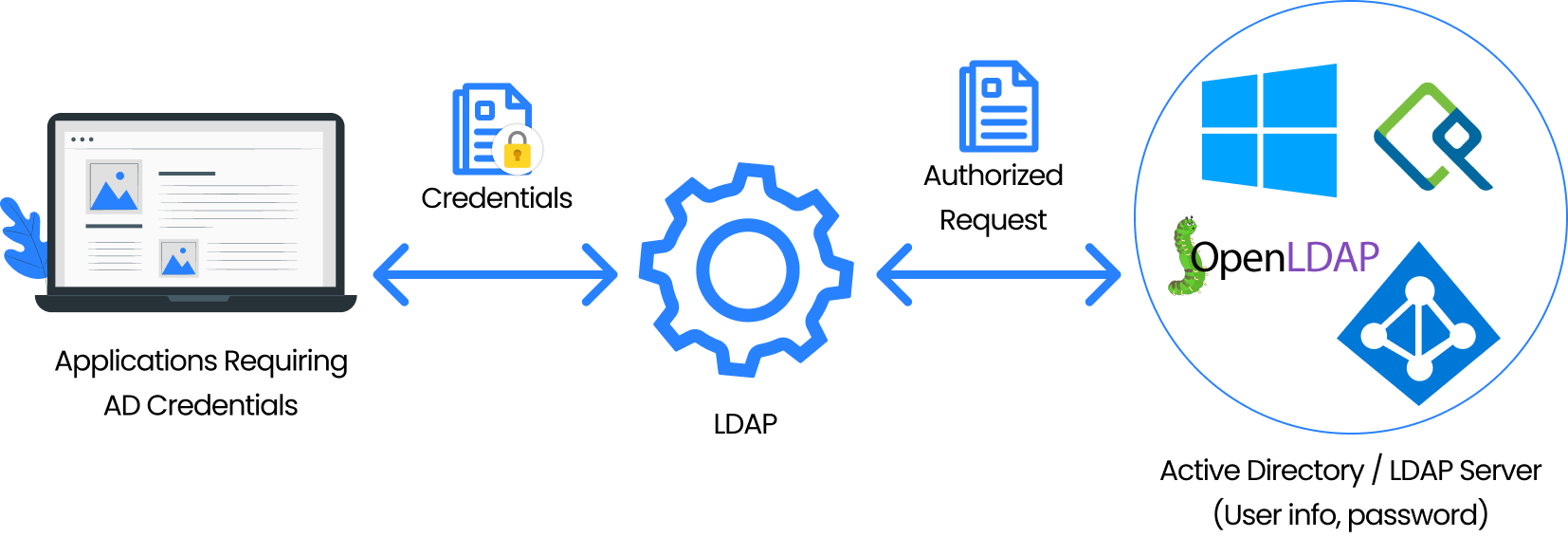
Users, Computers, and various resources within a network may all be managed centrally with Active Directory (AD) or any LDAP Server, which is both a database and a collection of services. Through the Active Directory/LDAP server, diverse users can connect with the network resources that are necessary for completing their tasks. Verifying the identity of a user requesting access to such resources or services can be accomplished using LDAP authentication via LDAP or LDAPS protocol. This same mechanism is often extended for the authentication of APIs.
In this API authentication process, users pass their login credentials, which are then authenticated from the Active Directory/LDAP server. The API returns a valid response upon a successful LDAP Authentication.
It's imperative to note that if the LDAP server becomes unavailable, the authentication process of all the dependent servers can be impacted which could further result in disruption of service. Because of this, it's recommended to configure a fallback LDAP server in your API Gateway.
Also, the configuration and integration of LDAP authentication on existing systems are slightly more complicated than the other API authentication methods. However, it becomes easier for organizations to integrate this method if they are already using Active Directory or any other LDAP server like OpenLDAP, FreeIPA, etc as their IDP (Identity Provider) throughout their IT infrastructure and further extend this for API Authorisation as well.
There are various other types of API authentication methods provided by XecureAPI that can be used to secure your API. As mentioned earlier, one should select the authentication method as per the application and security requirements.
To get detailed insights about our API Security Features, feel free to contact our experts.