With an increasing inclination toward microservices, the dependence of organizations on APIs has increased significantly. In fact, as per a survey conducted by Postman, 43% of the respondents said that APIs generate more than a quarter of their company’s revenue.
But as the dependence on APIs increases, they come under the prying eyes of hackers. To tackle this, OWASP, a non-profit community that produces content on web application security, publishes a list of the top 10 API risks every few years. This write-up will compare OWASP's top 10 API vulnerabilities of 2019 and OWASP's top 10 API vulnerabilities of 2023. The below infographic gives a brief idea of the API risks listed in 2019 and 2023.
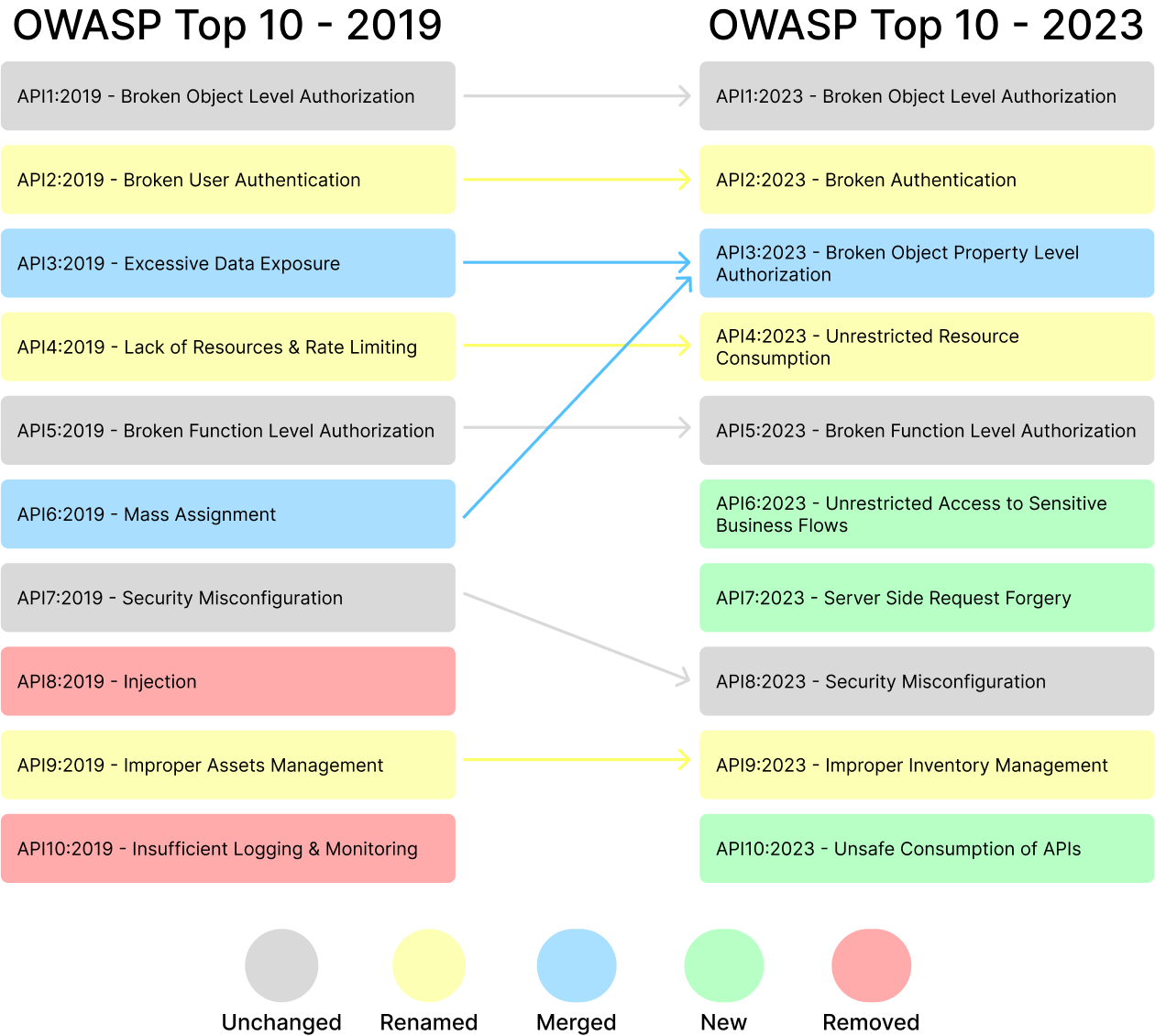
From the looks of it, it’s clear that some of these vulnerabilities are dominating the same position however, a few are updated, changed, or clubbed. Let’s review each vulnerability from the 2023 list and check its 2019 history.
API1: Broken Object Level Authorization (Unchanged)
Broken Object Level Authorization, abbreviated as BOLA, has been ranking first since 2019. This attack usually occurs due to improper authorization at the object level. This gives a greater attack surface for hackers as the endpoints that handle the object identifiers are exposed to them.
Microsoft Exchange faced a BOLA attack in 2021. By exploiting this vulnerability, the hackers bypassed a few access control points and were able to access sensitive information that was stored in the Microsoft Exchange servers. That data included user credentials and email communications. The attack impacted tens of thousands of companies across the globe.
This API security risk can be mitigated by:
- Implementing strong authentication and authorization protocols at each access point
- Regularly conducting security audits
- Monitoring and logging API activities
API2: Broken Authentication (Updated)
Broken authentication has also been fixed at the second position since 2019. The only change in this vulnerability is its name. It is mentioned as broken user authentication in the OWASP 2019 API security risks list. The nature of the attack has remained the same in recent years.
If the authentication process is not appropriately crafted, a hacker can use multiple ways including credential stuffing, unhashed passwords, brute-forcing, and session hijacking to attack the API and access sensitive data.
In 2015, Dunkin’ Donuts was in the news as it faced a brute force attack. The attackers targeted its digital customer account. They used customer information that was leaked and stolen earlier and ran a brute-force algorithm. The hackers got access to over 19,000 accounts and stole tens of thousands of reward cash using customer loyalty applications.
This API security risk can be mitigated by
- Using secure storage for credentials
- Introducing strong password policies
- Conducting frequent security testing
- Implementing multi-factor authentication
API3: Broken Object Property Level Authorization (Updated)
Excessive data exposure from the OWASP 2019 security risk list is replaced by broken object property level authorization in the OWASP 2023 security risk list. This vulnerability is a combination of excessive data exposure and mass assignment which ranked at third and sixth position in the 2019 list respectively.
When allowing the user to access any API endpoints, it's important to authenticate if the user has permission to access the specific object properties. If one fails to have proper authentication at this level, sensitive data can be exposed to attackers.
Twitter has been a victim of an attack that exploited broken object property level authorization vulnerability. The social media giant provides an API that allows the exchange of a Twitter ID for associated email addresses and phone numbers. However, this practice raises concerns about excessive data exposure, as obtaining a Twitter ID can be further used to fetch user information. The social media company released a statement in August 2022 that the vulnerability was spotted by its bug bounty in January 2022. However, an attacker exploited this vulnerability in July 2022 and they offered to sell that data.
This API security risk can be mitigated by:
- Validating user permissions before providing access to object properties
- Implementing proper authorization checks
- Monitoring and logging object property access
API4: Unrestricted Resource Consumption (Updated)
Known as Lack of Resources and Rate Limiting in the OWASP 2019 API vulnerabilities, is now called unrestricted resource consumption in the 2023 API risk list of OWASP. The former only focused on vulnerabilities however, the latter speaks about the consequences of ignoring proper rate limits and restrictions on the usage of resources.
By exploiting this API vulnerability, the attacker can exhaust the resources of the target system using denial-of-service (DoS) attacks. They send a large number of requests to the targeted API which can either make the system unavailable or unstable. Poland's key tax portal had fallen prey to a DDoS attack recently. Attackers targeted the resources that support the APIs behind the central tax service. Due to this, the server became unavailable for several hours.
This API security risk can be mitigated by
- Monitoring and analyzing the usage of resources
- Conducting input validation and sanitization
- Implementing throttling and rate limiting
API5: Broken Function Level Authorization (Unchanged)
This vulnerability has been in the fifth position in both OWASP 2019 and 2023 API security risks list. Broken function level authorization vulnerability is exploited when a user is allowed to perform tasks that must be allowed to administrators only. This happens when the hierarchical permission system for users is not integrated properly.
The September 2022 Optus Data Breach happened due to publicly exposed and unprotected APIs. Three major security flaws caused the attack. First, they had public-facing APIs. Second, these APIs provided easy access to sensitive customer data. Lastly, the customer IDs were assigned in an incriminating fashion. The vulnerability was exploited for about three months which caused a risk of compromising data of 9.8 million customers.
This API security risk can be mitigated by
- Using role-based access control
- Keeping a regular check on access control policies
- Implementing robust authorization checks on all API end-points
API6: Unrestricted Access to Sensitive Business Flows (New)
In the OWASP 2019 API security risks list, Mass Assignment held the sixth position. However, it was replaced by Unrestricted Access to Sensitive Business Flows in 2023. Every company has its business workflow. The use of an API that provides excessive access to these sensitive business flows may allow attackers to identify vulnerabilities in the workflow and disrupt its proper operation.
Symantec, a cybersecurity company has also fallen victim to attacks caused due to this vulnerability by exploiting access control in the business logic of a reseller. They exposed private keys which which revoked 20,000 SSL certificates.
This API security risk can be mitigated by
- Implementing robust API authentication and authorization
- Identifying and classifying sensitive business processes in the APIs
- Giving minimum necessary permissions to users to perform the tasks
- Frequently monitoring API access logs
API7: Server-Side Request Forgery (New)
Server-side request forgery (SSRF) has replaced security misconfiguration from the 2019 API security risks list at the seventh position. This attack can occur when an attacker can manipulate requests on the server side which gives them access to internal resources and can further engage in malicious activities.
CapitalOne, an American bank holding company became a victim of SSRF in 2019. The presence of bugs in the infrastructure and poor security practices were the major reasons behind the attack. The attackers were able to leak more than 100 million customer records.
This API security risk can be mitigated by
- Validating the inputs given by the user that are used in server-side requests
- Restricting the requests that can access API endpoints by implementing stringent access control
- Implementing strong firewall configuration to limit access to the internal system.
- Monitoring and logging server-side requests
API8: Security Misconfiguration (Unchanged)
Injection attack is at the eighth position in the 2019 API Security risks of OWASP which was replaced by security misconfiguration which ranked seventh earlier. As the name suggests, the risk occurs when APIs are not configured securely, which may lead to potential security vulnerabilities and breaches. This may involve default settings, unprotected sensitive information, redundant functionalities, and poor access restrictions, which attackers could use to obtain unauthorized access, compromise data, or interrupt services.
JIRA, a collaboration tool, had a security misconfiguration, making personal and corporate data of many huge companies vulnerable to attack. The attack space was created because of authorization misconfiguration in Global Permissions.
This API security risk can be mitigated by
- Updating and patching all software components regularly
- Restricting access permissions to those necessary for the operations of APIs
- Implementing proper input validation and CORS configuration
- Frequently reviewing and updating API configurations
API9: Improper Inventory Management (Updated)
Improper Inventory Management also called Improper Assets Management in the 2019 list of OWASP occurs when the APIs are not inventoried or managed properly which creates a scope of multiple blind spots and a greater attack surface. It can expose business logic and resources which can create more vulnerabilities.
Optus, an Australian telecommunications company, fell victim to attacks due to improper inventory management in September 2022. The API used to manage customer accounts was targeted by the attackers which gave them access to critical information about customers including names, phone numbers, and addresses. The vulnerability had gone undetected due to improper management of APIs which jeopardized the sensitive information of thousands of customers.
This API security risk can be mitigated by
- Implementing an inventory management system
- Conducting frequent audits to verify the inventories’ accuracy
- Decommissioning unused APIs to reduce attack surface
API10: Unsafe Consumption of APIs (New)
Unsafe consumption of APIs has replaced insufficient logging and monitoring in the OWASP 2023 API security risks list. If the data received from external APIs is not validated and sanitized this vulnerability can occur. Attacks through unsafe API consumption occur when an API follows unsafe redirection, blindly supports third-party integrations, and trusts all the incoming data without proper validation.
Log4Shell vulnerability is one of the most recent and famous examples of unsafe consumption of APIs. Apache Log4j logging library is widely used across the globe and it allows non-restricted access from user control inputs over APIs. The flaw in the code allowed users to run arbitrary code on the servers hosting the application. Attackers were able to exploit this flaw by sending malicious code in the requests.
This API security risk can be mitigated by
- Implementing stringent input validation and sanitization process
- Using a secure communication protocol
- Monitoring and logging API communications using API Gateway
In conclusion, the OWASP 2023 API security risks list is majorly inclined towards controlling access. If we observe, we can notice that four risks are focused on providing access, three of them lean towards limiting it and the remaining three are talking about setting up the APIs securely and validating and sanitizing the incoming requests.
Technology is advancing at a rapid pace but so are the techniques of cybercriminals. It's always advisable to stay ahead of the attackers.
Protect your APIs today. Contact the team at XecureAPI Gateway to know how your APIs and data can be safeguarded.


